Cyber Briefing: 2025.12.24
Loader malware, Android SMS theft, Iranian APT resurgence, healthcare ransomware, global fraud convictions, North Korea crypto theft, and Google lawsuits dominated.
👉 What’s the latest in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Cracked Software Spreads Loader Malware
Cybersecurity researchers have uncovered a new campaign that delivers a stealthy, modular malware loader called CountLoader through websites offering cracked software. This sophisticated attack chain uses the loader to establish initial access and evade security measures before deploying secondary payloads like info-stealers or remote access trojans.
2. Android Malware Combines Droppers SMS RAT
Threat actors are deploying a sophisticated SMS stealer known as Wonderland to target mobile users in Uzbekistan through malicious dropper apps. These applications bypass security measures by disguising themselves as harmless files or well-known platforms like Google Play to gain control over user messages and sensitive data.
3. Iranian Infy APT Returns With New Malware
Security researchers have identified a resurgence of the Iranian threat actor Infy, also known as Prince of Persia, which has remained active and dangerous despite years of low visibility. The group is currently employing sophisticated malware updates and resilient infrastructure to target high-value victims across several countries including Iran, Iraq, Turkey, India, and Canada.
For more alerts click here!
💥 Cyber Incidents
4. Baker University Data Breach Hits 53,000
The Iranian threat actor known as Infy or Prince of Persia has resurfaced with updated malware and expanded operations after several years of relative silence. Security researchers have identified a covert campaign targeting victims across multiple continents using resilient infrastructure and sophisticated command and control mechanisms.
5. NHS England Tech Provider Confirms Breach
DXS International, a UK-based healthcare technology provider for the National Health Service, recently disclosed a cyberattack affecting its office servers that was first discovered on December 14. Although the ransomware group DevMan claims to have stolen 300 gigabytes of data, the company maintains that front-line clinical services remain fully operational with minimal impact on overall operations.
6. Netstar Australia Hit By Ransomware
Netstar Australia, a Melbourne-based fleet management and telematics provider, has fallen victim to a data extortion attack by the Blackshrantac ransomware group. The incident highlights the growing cybersecurity vulnerabilities within the telematics industry, which manages highly sensitive GPS and operational data for government and critical infrastructure sectors.
For more incidents click here!
📢 Cyber News
7. Nigerian National Convicted Of Fraud
A federal jury in Maryland convicted Nigerian national Olusegun Samson Adejorin for orchestrating a sophisticated 7.5 million dollar fraud scheme targeting two charitable organizations. Adejorin, who was extradited from Ghana, now faces a significant prison sentence for wire fraud, identity theft, and unauthorized computer access.
8. North Korean Hackers Steal 2B Crypto
North Korea-linked hackers stole a record $2 billion in cryptocurrency during 2025, marking a 51% increase from the previous year and bringing their total historical haul to $6.75 billion. This surge was driven by a strategic shift toward fewer but more massive attacks on centralized services, exemplified by a single $1.4 billion breach of the Bybit exchange.
9. Google Sues Chinese Text Scam Group
Google has filed a lawsuit against a Chinese-speaking cybercriminal group known as Darcula that is allegedly responsible for a massive wave of phishing text messages targeting Americans. The legal action seeks court authorization to seize the group’s web infrastructure and shut down operations that impersonate major organizations to steal credit card information.
For more news click here!
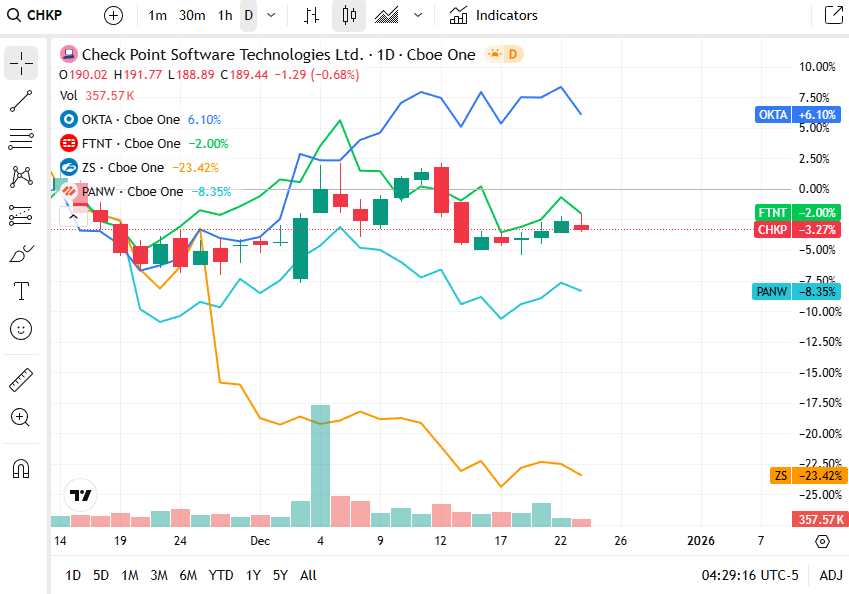
📈Cyber Stocks
On Wednesday, 24th December, cybersecurity stocks traded mostly lower as broader market caution and profit-taking influenced performance across tech and defensive names. Despite sustained enterprise demand for cloud, identity and perimeter security, mixed sentiment and rotation into other sectors kept sector gains constrained.
Check Point Software Technologies closed at 189.44 dollars and edged lower, with mixed sentiment in defensive names tempering the session despite steady demand for perimeter and firewall defenses.
Okta closed at 89.06 dollars and slipped, as identity-security spending held up but broader market pressures kept the stock from extending recent strength.
Fortinet closed at 80.66 dollars and moved lower, as profit-taking and broader tech sector weakness pressured the stock despite ongoing interest in zero-trust and network-security solutions.
Zscaler closed at 229.32 dollars and dipped, reflecting light selling amid broader caution even though cloud-delivered security and zero-trust adoption remained robust.
Palo Alto Networks closed at 188.12 dollars and eased modestly, with broader market volatility outweighing continued confidence in its unified AI-driven security platform and enterprise demand.
💡 Cyber Tip
🎥 Cracked Software Downloads Spread Loader Malware
Downloading cracked software or tools promoted in YouTube videos can silently install loader malware like CountLoader. These loaders open the door to data theft, persistent access, and full system compromise without obvious warning signs.
🔐 What You Should Do
Only download software from official vendor websites or trusted app stores
Block pirated or unauthorized software using endpoint and policy controls
Disable or closely monitor scheduled tasks and suspicious binaries like mshta.exe
Keep endpoint security tools updated and review alerts for persistence activity
⚠️ Why This Matters
Loader malware is often just the first stage of an attack. Once installed, it gives attackers long-term access to deploy ransomware, steal credentials, or remotely control systems while staying hidden.
📚 Cyber Book
Digital Divas by Catherine Kinloch
That concludes today’s briefing. You can check the top headlines here!
Copyright © 2025CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium