Cyber Briefing: 2026.01.06
Fake booking emails spread RATs as VS Code supply chain risks grow, breaches hit ISPs and crypto users, deepfake probes rise, and biometrics expand.
👉 What’s happening in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Fake Booking Emails Push Hotels To DCRat
Cybersecurity researchers recently identified a campaign named PHALT#BLYX that uses fake blue screen of death errors to target the European hospitality sector. This multi-stage attack tricks victims into executing malicious commands that ultimately install the DCRat remote access trojan on their systems.
2. VS Code Forks Expose Open VSX Risks
Several popular AI-powered code editors that are based on Visual Studio Code have been found to suggest extensions that do not exist on the Open VSX registry. This security gap allows attackers to register those unclaimed names and distribute malicious software to unsuspecting developers who follow the editor’s built-in recommendations.
3. Cloud File Sharing Sites Targeted For Theft
AI-powered coding tools like Cursor and Trae are vulnerable to supply chain attacks because they recommend extensions that do not exist on the Open VSX registry. This allows malicious actors to claim these empty namespaces and trick developers into installing harmful software that can steal source code or credentials.
For more alerts click here!
💥 Cyber Incidents
4. NordVPN Denies Breach After Data Leak
NordVPN has dismissed claims of a system breach following reports that a hacker leaked data supposedly taken from a development server. The threat actor alleged that they gained access to source code and internal information by brute-forcing a misconfigured server that lacked multi-attribute authentication.
5. Brightspeed Probes Possible Cyberattack
Brightspeed is currently looking into reports of a data breach following claims from a hacking group known as Crimson Collective regarding the theft of customer records. The group alleges it has obtained sensitive personal and billing information belonging to more than one million users across the company’s twenty-state service area.
6. Ledger Customers Hit By Global E Breach
Ledger recently notified customers that their personal information was leaked following a security breach at Global-e, a third-party payment processor used for transactions on Ledger’s website. The company clarified that while customer contact details were accessed, Ledger’s own internal systems and hardware security remain uncompromised.
For more incidents click here!
📢 Cyber News
7. Bitfinex Hack Perpetrator Freed Early
Ilya Lichtenstein, the mastermind behind the 2016 Bitfinex cryptocurrency hack, has been released early from federal prison and placed into home confinement. His shortened sentence is attributed to the First Step Act, a criminal justice reform law that allows inmates to earn credits for rehabilitation and good behavior.
8. France Probes AI Undressing Deepfakes
French authorities have launched an investigation into sexually explicit deepfakes created using the Grok AI tool on the social media platform X. The probe follows reports from hundreds of women and teenagers whose photos were manipulated into “undressed” images and shared online without their consent.
9. NYC Wegmans Stores Facial Scan Data
Wegmans has introduced biometric surveillance signs in its Brooklyn and Manhattan locations, notifying customers that facial scans and other identifying data are being collected for security purposes. While the company claims the technology is limited to high-risk stores to identify individuals with a history of misconduct, the updated policy no longer promises that shopper data will not be stored.
For more news click here!
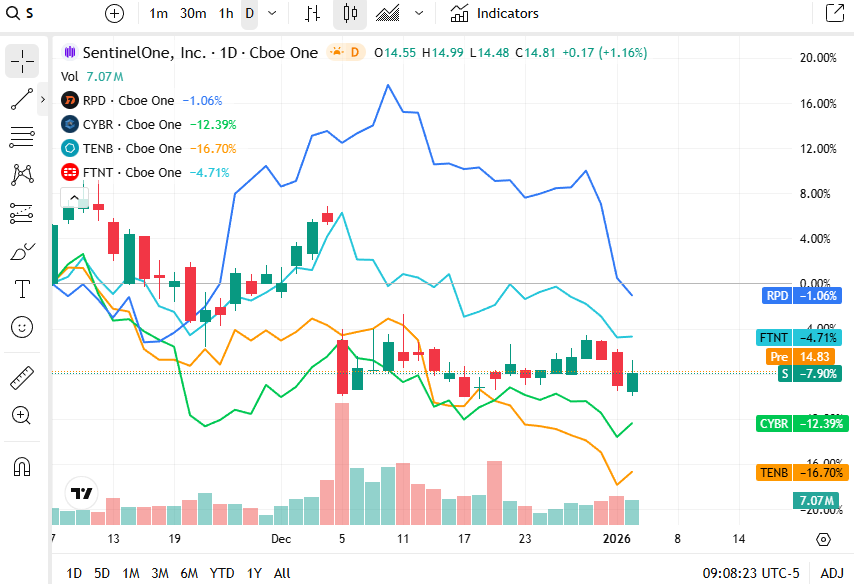
📈Cyber Stocks
On Tuesday, 6th January, cybersecurity stocks overall traded with modest strength as investor interest in defensive technology remained evident amid broader market volatility. Continued enterprise demand for cloud security, identity and perimeter defenses supported sector performance, even as profit-taking and rotation influenced several names.
SentinelOne closed at 14.81 dollars and inched higher, reflecting continued investor interest in AI-driven endpoint detection and response solutions despite broader caution in tech.
Rapid7 closed at 14.05 dollars and eased slightly, as profit-taking and rotation influenced near-term trading even though enterprise investment in vulnerability-management and detection-response services remained steady.
CyberArk Software closed at 441.46 dollars and moved higher, supported by strong enterprise demand for privileged access management and identity security as organisations prioritise securing credentials and high-risk accounts.
Tenable Holdings closed at 23.05 dollars and gained modestly, supported by ongoing enterprise focus on vulnerability scanning and risk prioritisation amid regulatory compliance pressures.
Fortinet closed at 77.94 dollars and was largely unchanged, with persistent interest in zero-trust and network-security solutions balancing broader market headwinds.
💡 Cyber Tip
🏨 Fake Booking Emails Push Hotels to DCRat
The PHALT#BLYX campaign targets European hotels using fake Booking.com cancellation alerts. Attackers trick employees into running malicious PowerShell code via a simulated system error screen to install the DCRat trojan. The malware hijacks legitimate Windows tools to bypass antivirus and establish a persistent foothold for data theft.
🔐 What You Should Do
Verify Links: Access management portals via bookmarks, never through email links.
Staff Training: Warn employees that legitimate support will never ask them to paste code into a Command Prompt.
Limit Permissions: Restrict administrative rights to prevent unauthorized system changes and antivirus tampering.
Monitor Binaries: Audit the use of tools like MSBuild and PowerShell for unusual network activity.
Block Scripts: Disable unsigned PowerShell scripts across all front-desk workstations.
⚠️ Why This Matters
This attack uses “Living-off-the-Land” techniques to hide inside legitimate processes, making it difficult for basic antivirus to detect. By targeting the hospitality sector, hackers gain access to sensitive guest information and financial systems, turning a simple phishing lure into a full-scale corporate breach.
📚 Cyber Book
Cybersecurity for Beginners by Raef Meeuwisse
That concludes today’s briefing. You can check the top headlines here!
Copyright © 2025CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium










Brillaint breakdown of the PHALT#BLYX campaign. The method of leveraging fake BSOD screens to socially engineer hospitality staff into running PowerShell commands is actually really clever becaues it exploits both technical trust and operational pressure in environments that can't afford much downtime. From what Ive seen in other sectors, the "living-off-the-land" approch using MSBuild and legit binaries makes this significantly harder to catch with traditional AV.