Cyber Briefing: 2026.01.07
Domain spoofing phishing surges as critical RCEs hit Veeam and n8n, insurers face breaches, ransomware claims grow, and arrests follow major leaks.
👉 What’s happening in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Microsoft Warns Of Domain Phishing
Cybercriminals are exploiting complex email routing and weak spoofing protections to send phishing emails that appear to come from within the target organization. By impersonating internal domains, these attackers bypass traditional scrutiny to deliver malicious links and documents that facilitate credential theft and financial fraud.
2. Veeam Patches Critical Backup RCE
Veeam has launched critical security patches for its Backup and Replication software to fix several vulnerabilities, the most severe of which allows for remote code execution. These flaws affect version 13.0.1.180 and earlier, making it essential for administrators to update to version 13.0.1.1071 to prevent potential unauthorized system access.
3. n8n Warns Of Critical RCE Flaw
The workflow automation platform n8n has disclosed a critical security vulnerability that could allow authenticated users to execute unauthorized code on its service. Assigned a maximum CVSS score of 10.0, the flaw affects both self-hosted and cloud-based instances across a wide range of versions released since version 0.123.0.
For more alerts click here!
💥 Cyber Incidents
4. Australian Gold Producer Hit Cyberattack
Regis Resources is a prominent Australian gold producer that recently confirmed a cyber intrusion involving its subsidiary, McPhillamys Gold. Although the Lynx ransomware group claimed responsibility for the attack on their leak site, the company maintains that no data was stolen and operations remain unaffected.
5. Prosura Insurer Hit By Cyber Breach
Insurer Prosura has confirmed a significant cyber incident involving unauthorized access to its systems and the compromise of customer personal data. The breach has prompted the company to disable its online self-service portal and halt all new policy sales while an investigation into the scope of the exposure remains ongoing.
6. Sedgwick Discloses Ransomware Breach
Sedgwick confirmed that a cyber incident recently affected its federal contractor subsidiary after the TridentLocker group claimed to have stolen several gigabytes of data. The company is currently investigating the breach and notifying relevant law enforcement and clients while maintaining that the rest of its global operations remain secure.
For more incidents click here!
📢 Cyber News
7. UK Plans To Boost Public Sector Cyber
The United Kingdom has launched a comprehensive cybersecurity strategy supported by 210 million pounds to harden defenses across government departments and public services. This initiative introduces a dedicated unit to manage risks and coordinate responses, ensuring that essential systems like healthcare and taxation remain protected against digital threats.
8. Microsoft Cancels Exchange Email Limits
Microsoft has officially scrapped its plan to restrict Exchange Online users to a daily maximum of 2,000 external recipients. This reversal follows significant pushback from customers who argued the restriction would disrupt legitimate business operations and bulk communication needs.
9. Desjardins Data Leak Suspect Arrested
Spanish authorities arrested Juan Pablo Serrano on November 6, 2025, ending a year-long international search for his alleged role in the massive Desjardins data breach. Serrano is accused of purchasing and using stolen personal information belonging to nearly 10 million clients of the Canadian financial institution.
For more news click here!
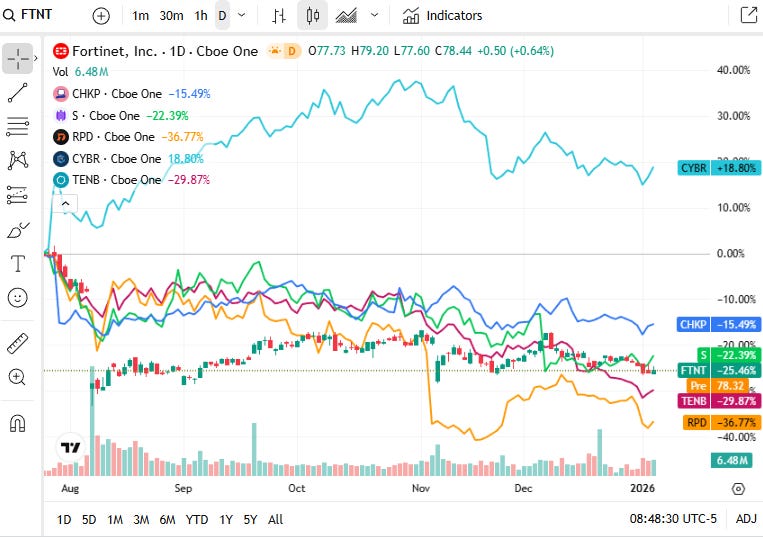
📈Cyber Stocks
On Wednesday, 7th January, cybersecurity stocks generally traded with mild strength as ongoing enterprise demand for cloud, identity and perimeter security helped support the sector amid broader market volatility. Continued investment in AI-enabled protection, zero-trust architectures and compliance initiatives provided stability, even as profit-taking capped broad gains.
Fortinet closed at 78.44 dollars and inched higher, supported by ongoing interest in zero-trust and network-security solutions even as broader market caution persisted.
Check Point Software Technologies closed at 186.01 dollars and moved higher, reflecting steady demand for perimeter and firewall defenses amid elevated global cyber-threat conditions.
SentinelOne closed at 15.18 dollars and nudged up, supported by investor interest in AI-augmented endpoint detection and response solutions as threat complexity rises.
Rapid7 closed at 14.36 dollars and gained modestly, with ongoing enterprise investment in vulnerability management and detection-response services underpinning steady demand.
CyberArk Software closed at 449.93 dollars and moved higher, buoyed by sustained demand for privileged access management and identity security tools as organizations focus on credential protection.
Tenable Holdings closed at 23.29 dollars and edged up, supported by continued enterprise focus on vulnerability scanning and risk prioritization amid regulatory compliance pressures.
💡 Cyber Tip
📧 Microsoft Warns of Internal Domain Phishing
Attackers are abusing weak spoofing protections and complex email routing to send phishing messages that appear to come from inside an organization. These emails often impersonate internal teams, bypass security checks, and deliver malicious links or attachments designed to steal credentials or commit financial fraud.
🔐 What You Should Do
• Enforce strict SPF, DKIM, and DMARC policies across all mail routes
• Review complex or hybrid email routing for spoofing gaps
• Be cautious of emails where sender and recipient domains look identical
• Treat internal looking emails with links or urgent requests as suspicious
• Train staff to spot fake HR, voicemail, and password reset messages
⚠️ Why This Matters
Internal looking phishing emails are far more convincing and can bypass both technical controls and human suspicion. Once attackers steal credentials, they can evade MFA, monitor communications, and launch high impact financial or data theft attacks from inside the network.
📚 Cyber Book
The Layman’s Guide to Cybersecurity by Travis Wolfe
That concludes today’s briefing. You can check the top headlines here!
Copyright © 2025CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium