Cyber Briefing: 2026.01.08
Multiple cyberattacks, data breaches, and malware campaigns continue to target organizations globally, ranging from Android botnets
👉 What’s happening in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Kimwolf Botnet Uses Proxies To Spread
The Kimwolf botnet has expanded to over two million infected Android devices by exploiting vulnerabilities in residential proxy networks and exposed debugging services. Primarily targeting streaming boxes and TV devices, the malware utilizes these compromised systems to launch massive DDoS attacks and monetize traffic through unauthorized proxy resale.
2. Cisco Patches ISE Flaw After PoC Leak
Cisco has issued security patches for a medium-severity vulnerability in its Identity Services Engine and ISE Passive Identity Connector following the release of a public proof-of-concept exploit. The flaw could allow an administrator to access sensitive files on the underlying operating system, prompting Cisco to urge users to update to protected versions immediately.
3. NodeCordRAT Found in npm Bitcoin Tools
Cybersecurity researchers recently identified three malicious npm packages uploaded by a user named wenmoonx that were designed to distribute a new remote access trojan dubbed NodeCordRAT. These packages, which mimicked legitimate cryptocurrency libraries to trick developers, utilize Discord servers for command-and-control operations and can steal sensitive data including crypto wallet seed phrases and browser credentials.
For more alerts click here!
💥 Cyber Incidents
4. Email Routing Flaw Enables Internal Phishing
Threat actors are bypassing security measures by taking advantage of complex email routing and weak spoofing protections to send fraudulent messages that appear to originate from within a victim’s own organization. By utilizing phishing-as-a-service platforms like Tycoon2FA, these attackers successfully deceive employees into providing credentials and bypassing multi-factor authentication through realistic internal lures.
5. School District Probes Cyberattack
Oakland Community School District 5 is investigating a holiday break cybersecurity attack where hackers unsuccessfully attempted to extort the district for payment. By working with technical experts and utilizing backup systems, officials restored operations without paying the ransom or compromising sensitive student and financial data.
6. Lone Hacker Used Infostealers At Firms
An Iranian hacker operating under the aliases Zestix and Sentap successfully breached the private data of 50 global corporations, including Iberia Airlines and Sekisui House, by using stolen credentials. The attacker is currently auctioning the compromised corporate information on dark web forums after exploiting the lack of multi-factor authentication on sensitive file-sharing platforms.
For more incidents click here!
📢 Cyber News
7. Crypto Scam Suspect Accused Of Billions
Authorities recently apprehended Chen Zhi in a foreign country following his indictment in a Brooklyn federal court for orchestrating a massive international cryptocurrency fraud. He is accused of defrauding American investors out of millions of dollars through an elaborate digital currency scheme.
8. DDoSia Fuels Affiliate Hacktivist Attacks
The pro-Russian hacktivist collective NoName057(16) utilizes a volunteer-driven platform called DDoSia to launch coordinated cyberattacks against Ukrainian and Western infrastructure. By gamifying the process and aligning operations with major geopolitical events, the group maintains a persistent and ideologically motivated botnet of non-technical supporters.
9. Stalkerware Operator Pleads Guilty
The owner of a Michigan-based company pleaded guilty to federal charges for selling pcTattletale, a surveillance software marketed to spy on romantic partners without their consent. This conviction marks the first successful criminal prosecution of a stalkerware operator in a decade, highlighting a significant shift in federal enforcement against the industry.
For more news click here!
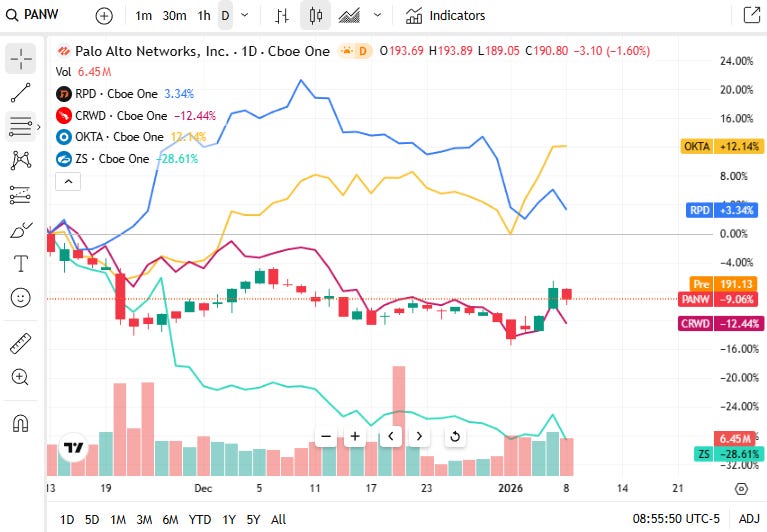
📈Cyber Stocks
On Thursday, 8th January, cybersecurity stocks generally traded higher as investor optimism returned to defensive technology names amid ongoing enterprise demand for cloud security, identity protection and perimeter defense. Strong interest in AI-enabled threat detection and platform consolidation also supported broad sector momentum.
Palo Alto Networks closed at 193.90 dollars and moved higher, reflecting sustained confidence in its unified AI-driven security platform and momentum in cloud and identity security.
CrowdStrike closed at 478.91 dollars and posted a strong gain, supported by continued demand for its cloud-native Falcon platform and advanced endpoint protection as organisations expand threat detection capabilities.
Okta closed at 93.84 dollars and climbed, buoyed by steady enterprise investment in identity and access management amid rising focus on identity-centric threats.
Zscaler closed at 231.16 dollars and advanced, driven by ongoing adoption of cloud-delivered security and zero-trust architectures as organisations modernise their security stacks.
Fortinet closed at 80.02 dollars and gained, supported by persistent interest in zero-trust and network-security solutions despite broader market rotation dynamics.
💡 Cyber Tip
📧 Cisco ISE Flaw After PoC Leak
Cisco patched a medium-severity ISE vulnerability after a public PoC showed how attackers with admin access could read sensitive operating system files.
🔐 What You Should Do
Apply Cisco’s latest ISE and ISE PIC patches immediately
Upgrade to a fixed release if running ISE versions earlier than 3.2
Patch affected Snort 3–based products (FTD, IOS XE, Meraki)
Review and limit administrative access to Cisco management interfaces
⚠️ Why This Matters
Public exploit code lowers the barrier to abuse, and unpatched Cisco infrastructure could expose sensitive system data or weaken perimeter defenses.
📚 Cyber Book
Digital Tidiness by Kara Johnson
Get book: https://amzn.to/4pqSmNG
That concludes today’s briefing. You can check the top headlines here!
Copyright © 2025CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium










Solid roundup! The Cisco ISE timing is telling because once PoC code drops, the window for exploitation shrinks fast. Perimeter defense has alway been about layering controls, but vulnerabilities in identity infra like ISE are especially nasty since they sit at the trust boundary. I've seen orgs treat these as"internal" systems and deprioritze patching, which is exaclty what threat actors count on.