Cyber Briefing: 2026.01.20
China-linked APT activity, critical plugin exploits, Cloudflare WAF bypass fixes, major data breaches, lost government devices, and global cybercrime arrests.
👉 What’s going on in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. China Linked APT Targets North American Infrastructure
A China-linked threat actor identified as UAT-8837 has been targeting North American critical infrastructure since early 2025. Cisco Talos reports that this group utilizes a sophisticated mix of zero-day exploits and open-source tools to map internal environments and maintain persistent access.
2. Cloudflare Fixes ACME Bug Enabling WAF Bypass
Cloudflare recently patched a security vulnerability within its Automatic Certificate Management Environment validation logic that allowed potential attackers to bypass web application firewall protections. By exploiting a flaw in how the edge network handled specific validation paths, unauthorized users could have gained direct access to customer origin servers despite existing security controls.
3. Critical Modular DS Plugin Flaw Enables Admin Takeover
A critical vulnerability in the Modular DS WordPress plugin, tracked as CVE-2026-23550, allows unauthenticated attackers to gain administrative access with a maximum CVSS score of 10.0. Security researchers have confirmed that threat actors are actively exploiting this flaw to take over websites that use the management tool.
For more alerts click here!
💥 Cyber Incidents
4. Grubhub Confirms New Data Breach Incident
Grubhub is currently investigating a new data breach and an associated extortion attempt following a security compromise linked to its Zendesk platform. This latest incident, attributed to the hacking group ShinyHunters, allegedly stems from credentials stolen during a previous attack on Salesforce applications.
5. Japanese Nuclear Regulator Loses Phone in China
Japan’s nuclear regulator is investigating the potential leak of confidential data after an employee lost a work-issued smartphone during a private trip to China. The device contained sensitive contact information for security personnel that is strictly guarded to maintain the integrity of national nuclear facilities.
6. Eurail Breach Exposes Passenger Info
Eurail recently confirmed a data breach involving customer information following notification emails sent to affected travelers this week. While the company initially posted an update on January 10, individuals only began receiving direct alerts on January 13 regarding the unauthorized access to their personal data.
For more incidents click here!
📢 Cyber News
7. Jordanian Man Admits Selling Network Access
A Jordanian man living in Georgia recently pleaded guilty in federal court to operating as a cybercriminal access broker. He admitted to selling unauthorized login credentials for the networks of at least fifty different companies to an undercover officer.
8. Ghana Arrests Nigerians Over Cybercrime
Ghanaian authorities have apprehended nine Nigerian nationals in Accra following a multi-agency crackdown on organized cybercrime operations across several residential areas. The raids successfully rescued 44 individuals who were reportedly being held against their will and forced to execute fraudulent online schemes.
9. Police Bust Thai Based Voice Phishing Ring
Authorities in Seoul recently dismantled a Thailand-based voice phishing organization responsible for stealing approximately 7 billion won from dozens of victims. Seven individuals associated with the operation were apprehended, with six remains in custody as police continue to investigate the full scope of the multi-million dollar fraud.
For more news click here!
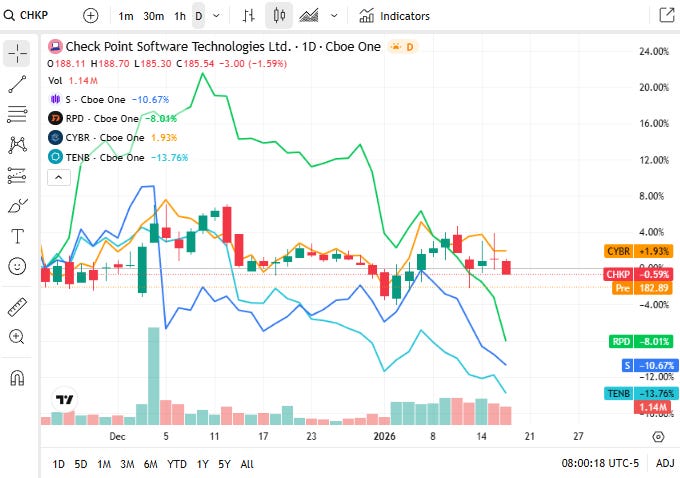
📈Cyber Stocks
For the U.S. market session on Tuesday, 20 January 2026, the cybersecurity sector showed mixed performance with moderate downward pressure as broader tech sentiment experienced light volatility.
Check Point Software Technologies closed at 185.54 dollars and eased, with defensive firewall and threat prevention demand sustaining interest while overall trading favored larger cloud-native peers.
SentinelOne closed at 13.90 dollars and was slightly lower, reflecting continued volatility in AI-enabled endpoint security valuations in a risk-off session.
Rapid7 closed at 12.64 dollars and declined, as vulnerability management and SIEM demand narratives compete with broader rotation out of smaller cap technology names.
CyberArk Software closed at 453.65 dollars and was flat to slightly higher, with identity security demand and potential acquisition integration narratives providing support relative to broader weakness.
Tenable Holdings closed at 22.12 dollars and was lower, in line with short-term underperformance among mid-cap security names despite persistent enterprise focus on risk and vulnerability management.
💡 Cyber Tip
☁️ Cloudflare Fixes ACME Bug Enabling WAF Bypass
Cloudflare has patched a flaw in its certificate validation logic that could have allowed attackers to bypass web application firewall protections. The issue involved the ACME HTTP-01 validation path, where improper checks could let certain requests reach customer origin servers without firewall inspection.
🔐 What You Should Do
Review origin server exposure and ensure access is restricted to Cloudflare IP ranges
Keep WAF rules and security settings enabled and regularly audited
Monitor logs for unusual traffic to certificate validation paths
Follow Cloudflare security advisories and change logs closely
⚠️ Why This Matters
Firewall bypass flaws undermine a key layer of defense. Even short lived gaps in validation logic can expose origin servers to reconnaissance or direct attack, making continuous monitoring and defense in depth essential.
📚 Cyber Book
Generative AI for Cybersecurity and Privacy by Youssef Baddi, Yassine Maleh, Izzat Alsmadi, Mohamed Lahby
That concludes today’s briefing. You can check the top headlines here!
Copyright © 2026 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium