Cyber Briefing: 2026.02.02
Supply-chain attacks poison software updates, crypto scams steal millions, energy sites face attacks, crime networks move billions, and Apple boosts privacy.
👉 What’s going on in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Notepad Plus Plus Update Spreads Malware
The lead developer of Notepad++ has confirmed that state-sponsored attackers hijacked the application’s update mechanism by compromising its hosting infrastructure. This sophisticated redirection allowed the threat actors to serve malicious files to specific users without exploiting any flaws within the Notepad++ code itself.
2. eScan Antivirus Updates Spread Malware
Unknown attackers compromised the update infrastructure of the Indian cybersecurity firm MicroWorld Technologies to distribute malware via its eScan antivirus software. While the company has since isolated the affected servers and released a patch, the breach allowed a persistent downloader to infiltrate numerous enterprise and consumer systems across South Asia.
3. Open Vsx Supply Chain Attack Spreads Glassworm
Cybersecurity researchers recently identified a supply chain attack on the Open VSX Registry where hackers hijacked a developer’s account to distribute malicious updates. These updates contained the GlassWorm malware loader, targeting over 22,000 users who had previously downloaded the legitimate versions of these developer tools.
For more alerts click here!
💥 Cyber Incidents
4. Nationstates Confirms Breach Shuts Site
The browser-based government simulation game NationStates recently experienced a significant data breach after a vulnerability reporter accessed and copied sensitive information from its production server. Although the individual responsible claimed to have deleted the stolen data, the site remains offline while developers rebuild the system to ensure its security.
5. Crypto Investor Loses Millions To Scam
An Ethereum investor recently lost $12.4 million in a sophisticated address poisoning scam after accidentally sending funds to a fraudulent wallet that mimicked a frequent contact. Security experts warn that this incident highlights the critical danger of copying wallet addresses from transaction histories rather than using verified address books.
6. Cyberattacks Disrupt Polish Energy Sites
CERT Polska reported that a coordinated wave of cyberattacks on December 29, 2025, targeted more than thirty renewable energy sites, a manufacturer, and a major combined heat and power plant. While the attackers successfully infiltrated both information technology and industrial control systems, their attempts at sabotage failed to disrupt the supply of electricity or heat to the public.
For more incidents click here!
📢 Cyber News
7. Arrests Trigger Scam Worker Exodus
Recent law enforcement actions against two major network leaders in Cambodia have triggered a massive release of thousands of laborers from illicit scam compounds. While this represents a significant disruption to the transnational pig-butchering industry, experts argue that these arrests are only a superficial fix for a deeply embedded criminal economy that continues to defraud victims globally.
8. Chinese Crime Networks Move Billions
In 2025, Chinese-language money laundering networks utilized cryptocurrency to move approximately 16.1 billion dollars in illegal funds, representing nearly twenty percent of all illicit digital asset activity. These sophisticated organizations leverage Telegram-based escrow platforms to facilitate a wide range of criminal trades, including human trafficking and the distribution of stolen assets.
9. Apple Privacy Feature Limits Tracking
Apple is launching a privacy setting in iOS 26.3 that allows users to restrict cellular carriers from tracking their exact location through cell towers. By toggling this feature on compatible iPhone and iPad models, the device will only share approximate neighborhood-level data with the network provider.
For more news click here!
📈Cyber Stocks
On Monday, 2 February 2026, cybersecurity stocks exhibited mixed early session performance as markets navigated ongoing tech rotation and persistent interest in security spending amid evolving threat landscapes.
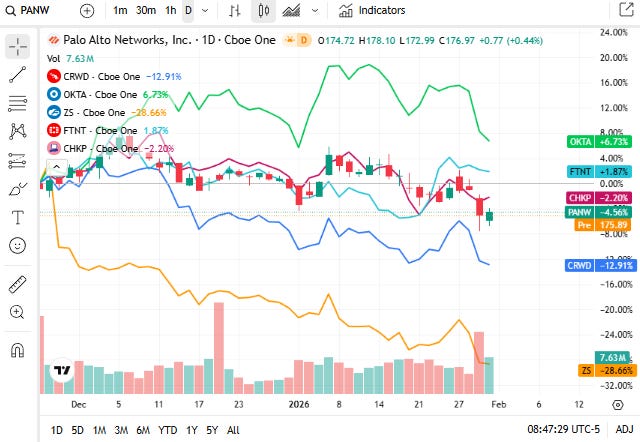
Palo Alto Networks closed around 176.97 dollars and was essentially flat, as platform and cloud security demand continues to underpin valuations in a cautious market.
CrowdStrike was trading near 441.41 dollars and was down modestly, reflecting some profit-taking in cloud-native endpoint and workload protection stocks.
Okta was around 84.48 dollars and moved lower, with identity and access management stocks showing early session softness.
Zscaler was near 200.01 dollars and edged down, as cloud security names tracked broader tech caution.
Fortinet was around 81.26 dollars and slightly lower, with network security hardware and services stocks modestly lagging peers.
Check Point Software Technologies was about 179.51 dollars and moved higher, supported by steady demand for defensive and integrated threat prevention solutions.
💡 Cyber Tip
📝 Notepad++ Update Mechanism Hijacked
Attackers compromised Notepad++ hosting infrastructure to hijack the update process and deliver malware to targeted users. The software itself was not exploited. Instead, update traffic was redirected to serve malicious files.
🛠️ What You Should Do
Download updates only from the official Notepad++ website
Verify installer signatures before running updates
Avoid third-party mirrors or legacy updaters
Monitor systems for unusual activity after updates
⚠️ Why This Matters
Compromised update channels turn trusted software into a malware delivery path, making supply chain attacks especially hard to detect.
📚 Cyber Book
This Is How They Tell Me the World Ends by Nicole Perlroth
That concludes today’s briefing. You can check the top headlines here!
Copyright © 2026 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium










The supply chain attack pattern here is revealing. Update mechanisms like Notepad++ and eScan got compromised because users inherently trust them, so attackers don't need sophisticated exploits. Reminds me of CDN hijacks in '22 where legitmate channels became vectors. The Okta vishing reference is particularly notable since identity laayers should be last-line defense, not another breach point.