Cyber Briefing: 2026.02.03
APT groups exploit Office flaws, vishing steals MFA, ransomware hits airports, Iran-linked ops target NGOs, extortion rises, and law enforcement seizures expand.
👉 What’s the latest in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. APT28 Exploits Office CVE 2026 21509
The state-sponsored Russian threat group APT28, also known as UAC-0001, is actively exploiting a newly discovered Microsoft Office vulnerability to target government entities in Ukraine and Eastern Europe. This campaign, labeled Operation Neusploit, uses malicious documents and server-side evasion to deliver specialized malware like the MiniDoor email stealer and the Covenant Grunt implant.
2. Mandiant Finds Vishing Attacks Stealing MFA
Mandiant has reported an increase in sophisticated extortion attacks linked to the hacking group ShinyHunters, which utilizes advanced social engineering to breach corporate environments. These attackers use fraudulent websites and phone-based phishing to steal login credentials and bypass security codes, ultimately aiming to steal data from cloud applications for ransom.
3. Iran Linked RedKitten Targets NGOs
An Iranian-linked group dubbed RedKitten is targeting activists and human rights observers using artificial intelligence to build malicious tools. The campaign exploits current civil unrest in Iran by using fake documents about deceased protesters to infect victims with a modular backdoor.
For more alerts click here!
💥 Cyber Incidents
4. Russian Ransomware Hackers Hit Tulsa Airport
The Russian ransomware group known as Qilin has reportedly breached the network of Tulsa International Airport and exfiltrated a significant volume of confidential organizational information. According to security researchers at Cybernews, the attackers have listed the airport on their leak site and provided nearly twenty data samples as evidence of the successful infiltration.
5. Ransomware Group Claims Hack of Software Company
Distinctive Systems, a UK-based software provider for the transport industry, is currently managing a cyber attack first identified in mid-January. Despite claims from the INC Ransom group and various trackers, the company has verified that no personal data from its Australian operations was compromised during the breach.
6. Cl0p Targets Australian IT Providers
The Cl0p cyber extortion group has targeted nine Australian companies by listing them on its darknet leak site following alleged links to two specific IT service providers. While the group threatens to publish stolen data soon, there are indications that the hackers may be attempting extortion without having actually compromised any sensitive information.
For more incidents click here!
📢 Cyber News
7. DOJ Seizes Domains Linked To Bulgarian Piracy
U.S. federal authorities recently seized three major internet domains registered in the United States that were being used to illegally distribute copyrighted content from Bulgaria. The operation, supported by international law enforcement, targeted sites responsible for millions of unauthorized downloads of films, television shows, and video games.
8. Canadian Hacker Steals $65M And Vanishes
A twenty-two-year-old Canadian math prodigy who allegedly stole sixty-five million dollars from decentralized finance platforms has disappeared after being apprehended in Serbia. Having previously earned a master’s degree at eighteen, the Hamilton native is now a fugitive once again following his escape from extradition proceedings in Belgrade.
9. Nobel Hacking Likely Leaks Winner Name
An investigation into the premature disclosure of Maria Corina Machado’s Nobel Peace Prize win has concluded that a cyber breach of the Nobel organization’s computer systems was the most probable cause. While the Norwegian Nobel Institute suspects an individual or state actor gained illegal access, they have declined to pursue a formal police investigation due to a lack of definitive evidence.
For more news click here!
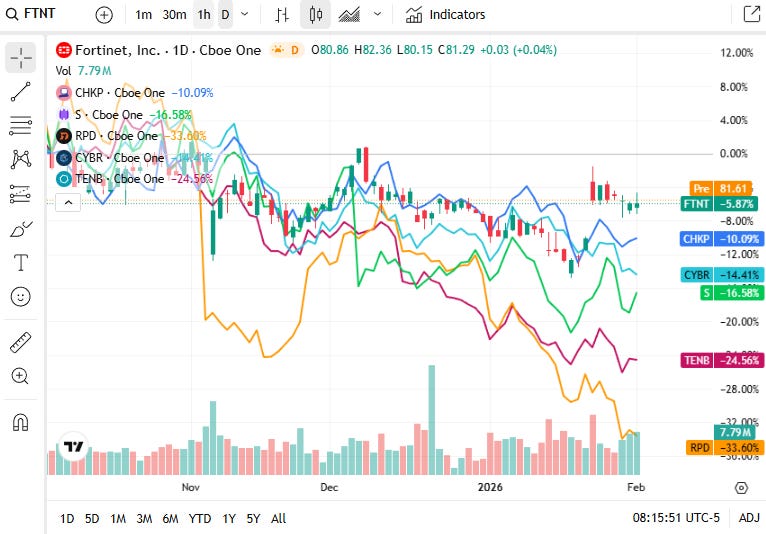
📈Cyber Stocks
Cybersecurity companies held mixed performance on Tuesday, 3rd of February as risk flows stayed uneven across technology sectors. Enterprise spending on cloud and zero-trust security remains a core positive driver, but near-term rotation within growth and safety-oriented tech weighed on pricings.
Fortinet finished around 81.29 dollars and was essentially flat, with network security demand steady although less dynamic than growth peers.
Check Point Software Technologies closed at 180.21 dollars and moved up, supported by defensive security demand and steady firewall platform positioning.
SentinelOne finished near 14.39 dollars and climbed, with AI-enabled endpoint protection stocks seeing selective buying.
Rapid7 closed at 11.80 dollars and was slightly lower, with vulnerability management and SIEM names under pressure amid mixed flows.
CyberArk Software ended around 427.27 dollars and moved down, as privileged access management valuations followed broader tech softness.
Tenable Holdings finished at 22.02 dollars and eased, reflecting mid-cap cybersecurity trends in a cautious session.
💡 Cyber Tip
📞 Mandiant Finds Vishing Attacks Stealing MFA
Mandiant reports a rise in vishing and phishing attacks linked to ShinyHunters, where attackers use fake login pages and phone calls to steal credentials and MFA codes in real time. Once inside, they target cloud apps to steal data and extort organizations.
🛠️ What You Should Do
Treat unsolicited IT or security calls as suspicious
Never share MFA codes or approve unexpected login requests
Use phishing-resistant MFA where possible
Monitor cloud access logs for unusual sign-ins
Train employees to verify support requests through official channels
⚠️ Why This Matters
MFA theft breaks one of the strongest security controls. When attackers bypass identity protections, they gain direct access to cloud data and can quickly escalate to extortion and data leaks.
📚 Cyber Book
Practical Fraud Prevention by Gilit Saporta ,Shoshana Maraney
That concludes today’s briefing. You can check the top headlines here!
Copyright © 2026 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium