Cyber Briefing: 2026.02.10
Asian state espionage spans 37 countries, routers and Signal targeted, Europe probes breaches and Big Tech, crypto fraud sentenced, and new tools block imposters.
👉 What’s trending in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Asian State Group Breaches 70 Gov Entities
A newly discovered cyber espionage group from Asia has breached the networks of 70 government and critical infrastructure organizations across 37 countries within the last year. Detailed analysis from Unit 42 reveals the group uses specialized malware and phishing tactics to exfiltrate sensitive military, financial, and diplomatic data on a global scale.
2. China-Linked DKnife Targets Routers
Cybersecurity researchers have uncovered DKnife, a sophisticated gateway-monitoring and adversary-in-the-middle framework utilized by Chinese threat actors since 2019 to target edge devices. The toolkit specializes in deep packet inspection and traffic manipulation to deliver malware, primarily focusing on Chinese-speaking users through localized phishing and application hijacking.
3. Germany Warns of Signal Phishing Attacks
German security agencies have issued a joint warning regarding a sophisticated phishing campaign on Signal that targets high-ranking political, military, and journalistic figures. The attack uses social engineering and deceptive device-linking tactics to hijack accounts, allowing state-sponsored actors to monitor communications and compromise broader professional networks.
For more alerts click here!
💥 Cyber Incidents
4. Spain Science Ministry Shuts Systems
The Spanish Ministry of Science has partially suspended its information technology systems and administrative services following a significant technical incident. While official statements remain vague regarding the cause, a threat actor has already claimed responsibility for a cyberattack and released sample data as evidence of a breach.
5. Norway Discloses Salt Typhoon Target
Norway’s domestic security agency has confirmed that the Chinese state-sponsored group Salt Typhoon successfully compromised various network devices within the country. The 2026 threat assessment identifies China, Russia, and Iran as major actors conducting cyber and hybrid operations to undermine Norwegian resilience and map critical infrastructure.
6. Hacker Attack Hits Uffizi Museum
The Uffizi Gallery in Florence successfully maintained public operations and visitor services after a weekend cyberattack targeted its internal administrative servers and staff email systems. While back-office functions faced disruption, the museum remained open to the public as ticketing and security systems were unaffected by the malware.
For more incidents click here!
📢 Cyber News
7. Fugitive Gets 20 Years In Crypto Scam
A U.S. judge sentenced Daren Li to 20 years in prison for orchestrating a 73 million dollar cryptocurrency fraud. The international scheme operated out of Cambodia and utilized social media and dating apps to target victims through social engineering.
8. EU Says TikTok Faces Major Fine
The European Commission has issued preliminary findings stating that TikTok is in breach of the Digital Services Act due to addictive design features like infinite scroll and autoplay. If these findings are confirmed, the social media giant faces potential fines of up to 6 percent of its global annual turnover unless it implements significant changes to its core service design.
9. New Tool Blocks Imposter Command Attacks
Tirith is a new cross-platform, open-source tool designed to prevent homoglyph attacks by inspecting shell commands for deceptive URLs before they execute. Available on GitHub and via npm, it integrates with shells like bash, zsh, and PowerShell to identify and block malicious characters or patterns that appear legitimate to the human eye.
For more news click here!
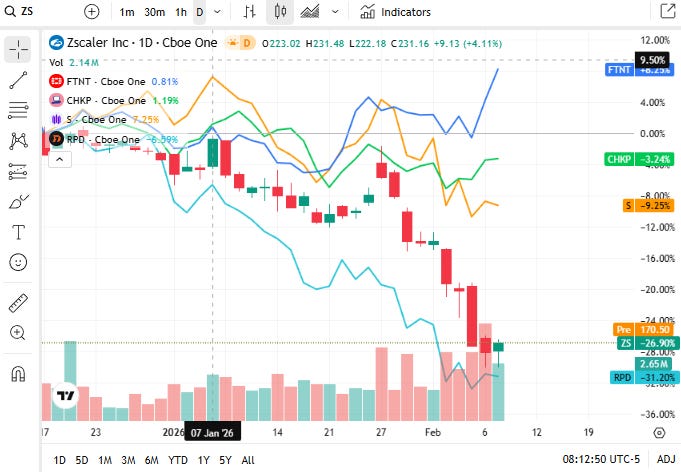
📈Cyber Stocks
Tuesday, 10 February 2026, the group broadly held gains from recent strength in enterprise security demand and rotation into defensive tech, with platform and cloud security leaders showing relative resilience even as broader market signals fluctuated. Structural tailwinds remain supportive amid accelerating digital threats and regulatory spend.
Zscaler ended at 170.18 dollars and was higher, as cloud security and zero-trust architectures held investor focus.
Fortinet finished near 85.93 dollars and moved up, with demand for network security and converged firewall solutions showing resilience.
Check Point Software Technologies closed at 181.27 dollars and was modestly higher, supported by steady demand for defensive threat prevention offerings.
SentinelOne finished at 13.14 dollars and was slightly lower, with smaller AI-enabled endpoint security names facing mixed flows.
Rapid7 closed at 10.76 dollars and was modestly lower, reflecting mixed sentiment in vulnerability management and SIEM exposure.
💡 Cyber Tip
🇩🇪 Germany Warns of Signal Phishing Attacks
German security agencies are warning of a sophisticated phishing campaign on Signal targeting political leaders, military officials, and journalists. Attackers abuse Signal’s legitimate device-linking features and social engineering tactics to hijack accounts, allowing them to spy on private communications and impersonate victims without deploying malware.
🛠️ What You Should Do
Never share Signal verification codes or PINs with anyone
Be cautious of messages claiming to be from Signal support or security bots
Enable registration lock and review linked devices regularly
Verify unexpected security requests through trusted offline channels
Treat QR codes for device linking as highly sensitive
⚠️ Why This Matters
Account takeovers on encrypted messaging apps give attackers direct access to sensitive conversations and contact networks. These human-focused attacks bypass encryption entirely, making vigilance and correct security settings the strongest defenses.
📚 Cyber Book
Phishing Dark Waters by Christopher Hadnagy, Michele Fincher
Copyright © 2026 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium