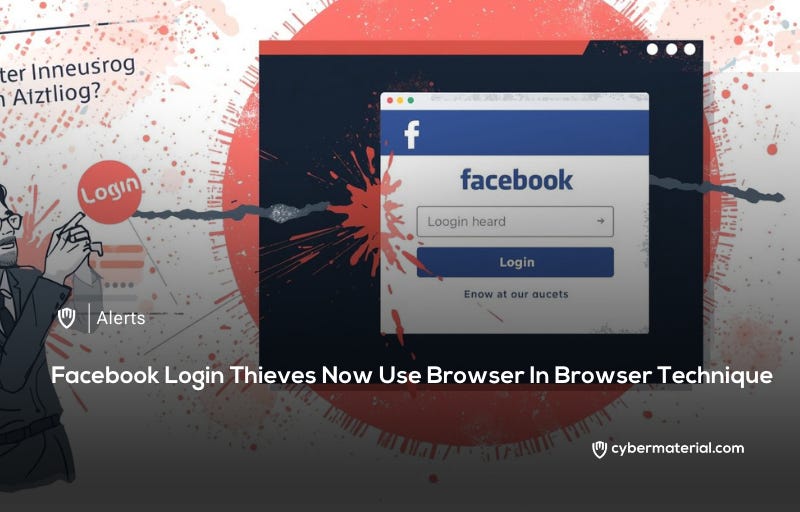
Recent trends show that hackers are frequently using the browser-in-the-browser phishing technique to steal Facebook login credentials from unsuspecting users. By creating fake pop-up windows that mimic legitimate login pages, cybercriminals can bypass traditional visual checks to harvest personal data and spread scams.
The browser-in-the-browser phishing technique was originally conceptualized by a security researcher in 2022 and has since been adopted by cybercriminals to target high-traffic platforms like Facebook and Steam. Because Facebook boasts billions of active users, it remains a primary target for threat actors looking to commit identity fraud or distribute malicious content. Security experts at Trellix have observed a significant uptick in these specific attacks over the last six months, noting that the stolen accounts are often used to further expand the reach of various fraudulent schemes.
In this specific type of attack, a user visits a website controlled by the hacker and is prompted to log in via a fake window. This window is not actually a separate browser instance but is instead an iframe coded to look exactly like a standard authentication pop-up. The attacker can customize this iframe with a realistic window title and a legitimate-looking URL, making it extremely difficult for the average person to distinguish the fake interface from a real one.
Recent campaigns have become more sophisticated by using social engineering themes to create a sense of urgency. Attackers often impersonate law firms sent to investigate copyright infringement or send fake security alerts from Meta warning of unauthorized logins. These messages typically threaten the user with immediate account suspension if they do not take action, which pressures the victim into interacting with the malicious link provided in the message.
To further enhance the illusion of legitimacy and evade security filters, hackers have integrated additional layers into their workflow. They frequently use URL shorteners to hide the true destination of malicious links and have even started including fake CAPTCHA pages branded with Meta logos. These extra steps serve to build trust with the victim before they reach the final stage of the phishing process, where the sensitive information is actually captured.
During the final phase of the attack, the victim is presented with the deceptive pop-up window and prompted to enter their Facebook username and password. Because the window appears to have the correct URL and branding, many users provide their credentials without hesitation. Once the information is entered into the fake form, it is sent directly to the attackers, who then gain full access to the compromised account and all associated personal information.
Source: Facebook Login Thieves Now Use Browser In Browser Technique