Cyber Briefing: 2026.01.27
Malicious Chrome and VS Code tools spread phishing, ClickFix abuses Windows, breach claims rise, AI content probes grow, and surveillance expands.
👉 What are the latest cybersecurity alerts, incidents, and news?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Malware Service Pushes Chrome Phishing
A new malware-as-a-service named Stanley enables attackers to create malicious Chrome extensions designed to bypass official security reviews for publication on the Chrome Web Store. These extensions use deceptive iframes to overlay phishing content on legitimate websites, allowing hackers to steal credentials while the browser address bar continues to display the original, trusted URL.
2. ClickFix Attacks Abuse Windows App V
Cybercriminals are now combining fake CAPTCHA prompts with signed Microsoft App-V scripts to bypass security and install the Amatera infostealer. This method uses a trusted Windows component to proxy malicious PowerShell commands, marking the first time this specific living-off-the-land technique has been seen in ClickFix campaigns
3. Malicious VS Code AI Extensions Steal Code
Security experts have identified two functional but malicious VS Code extensions disguised as AI coding tools that are secretly exfiltrating developer source code to Chinese servers. Despite their legitimate features, these tools—which have over 1.5 million combined installs—systematically capture and transmit every file edit and workspace modification without user consent.
For more alerts click here!
💥 Cyber Incidents
4. China Hacked Downing Street Phones
British media reports indicate that Chinese state-sponsored hackers allegedly targeted the mobile phones of senior aides to multiple UK prime ministers over several years. These claims emerge just as Prime Minister Keir Starmer prepares for a high-stakes diplomatic visit to China aimed at revitalizing economic ties.
5. Nova Claims Hack Of KPMG Denied
KPMG has addressed allegations from the Nova hacking collective regarding a purported data breach of its Dutch operations. While the group claims to have compromised the firm’s systems, KPMG explicitly stated that its managed infrastructure and security remains secure and uncompromised.
6. Waltio Faces Ransom Threat From Hackers
French crypto tax platform Waltio is currently facing a data extortion threat from the hacking collective ShinyHunters, which claims to have stolen personal information belonging to approximately 50,000 users. While the group is threatening to release 2024 tax reports, Waltio maintains that its core production systems remain secure and that no private financial credentials or crypto keys were accessed.
For more incidents click here!
📢 Cyber News
7. EU Probes X Over Grok Sexual Images
The European Commission has initiated a formal investigation into X under the Digital Services Act to determine if the platform failed to assess the risks of its Grok AI tool before deployment. This probe follows reports that the AI was used to generate sexually explicit content, including material that may constitute child sexual abuse.
8. Landmark Trial Tests Social Media Harm
A Los Angeles jury is now considering whether platforms like Instagram and TikTok are directly responsible for causing mental health disorders in teenagers. This personal injury trial, the first of its kind to reach a courtroom, parallels historic legal battles against big tobacco and pharmaceutical companies regarding product addiction and public welfare.
9. Long Island Unveils Police Command Center
Smithtown has launched a centralized surveillance hub that integrates over 250 cameras to monitor parks, marinas, and municipal buildings in real time. While local leaders defend the system as a necessary tool for crime prevention and emergency response, some residents have expressed deep privacy concerns, comparing the omnipresent monitoring to dystopian fiction.
For more news click here!
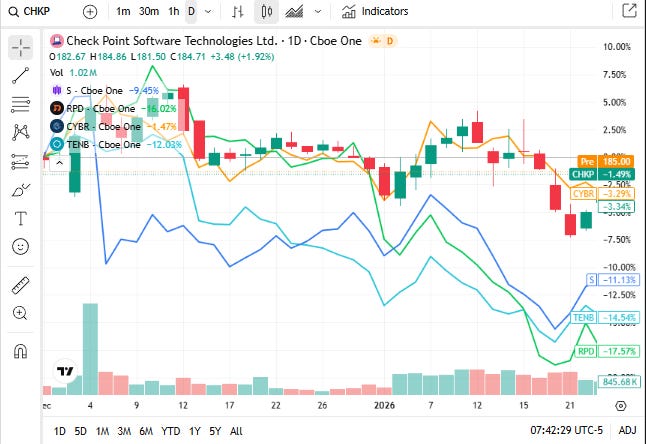
📈Cyber Stocks
U.S. equities in cybersecurity showed mixed performance heading into Tuesday, January 27, reflecting persistent demand signals but rotation pressures across growth sectors. Structural cybersecurity spending remains resilient, while near-term risk appetite varied amid mixed macro cues.
Check Point Software Technologies closed at 184.22 dollars and advanced, held up by steady threat prevention and firewall business momentum.
SentinelOne closed at 14.49 dollars and edged up, as AI-enabled endpoint protection stocks saw selective buying.
Rapid7 closed at 12.78 dollars and was slightly higher, with vulnerability management and SIEM exposure attracting modest support.
CyberArk Software closed at 448.49 dollars and trended higher, supported by privileged access management demand in identity-centric security frameworks.
Tenable Holdings closed at 23.06 dollars and moved up, with risk and exposure management names participating in broader sector strength.
💡 Cyber Tip
🖥️ ClickFix Attacks Abuse Windows App-V
Attackers are combining fake CAPTCHA prompts with a trusted Windows App-V script to install the Amatera infostealer. By tricking users into pasting commands into the Run dialog, the malware abuses a Microsoft-signed script to proxy malicious PowerShell activity, helping it evade traditional security tools and execute payloads directly in memory.
🛠️ What You Should Do
Train users never to copy and paste commands from websites or popups
Monitor for unusual execution of App-V scripts and wscript.exe
Restrict or audit PowerShell usage, especially hidden or 32-bit instances
Watch for unexpected outbound connections to trusted services like Google
Use EDR capable of detecting living-off-the-land abuse and in-memory execution
⚠️ Why This Matters
This technique turns trusted Windows components into malware delivery tools. By blending social engineering with signed system scripts and fileless execution, attackers can steal data while bypassing many traditional defenses, making user awareness and behavioral detection critical.
📚 Cyber Book
The Fraud Fighter’s Handbook by Nate Seidel
That concludes today’s briefing. You can check the top headlines here!
Copyright © 2026 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium