Cyber Briefing: 2026.01.26
North Korea targets blockchain devs, FortiGate and VMware exploits spread, major breach claims surface, phishing grows, and tech giants probe failures.
👉 What are the latest cybersecurity alerts, incidents, and news?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Konni Hackers Use AI Backdoor Targeting Blockchain
The North Korean cyber group Konni has expanded its global reach by using AI-generated PowerShell malware to target blockchain developers across Japan, India, and Australia. These sophisticated campaigns utilize malicious email links and legitimate advertising redirection services to bypass security filters and deploy remote access tools for persistent system control.
2. Fortinet Confirms Active FortiGate SSO Bypass
Fortinet is currently developing a comprehensive fix for a FortiCloud SSO authentication bypass vulnerability after discovering that attackers are successfully targeting already patched firewalls. The company’s security team identified a new attack path that allows hackers to circumvent existing security updates and gain unauthorized access through manipulated SAML messages.
3. CISA Warns VMware RCE Now Exploited
CISA has issued an urgent mandate for federal agencies to patch a critical remote code execution vulnerability in VMware vCenter Server by February 13th. Both Broadcom and federal officials confirmed that attackers are actively exploiting this flaw, which allows unauthorized users to gain control over virtual management systems without any user interaction.
For more alerts click here!
💥 Cyber Incidents
4. Crunchbase Confirms Data Breach Claims
Crunchbase has officially confirmed a security breach following the unauthorized publication of corporate data by the cybercrime group ShinyHunters. The hackers claim to have exfiltrated over 2 million records and released a significant volume of compressed files after the company declined to meet their ransom demands.
5. ShinyHunters Claim Okta SSO Hacks
The ShinyHunters extortion group has claimed responsibility for a series of voice phishing attacks targeting employees at major organizations using Okta, Microsoft, and Google for single sign-on services. By impersonating IT support staff, the attackers trick victims into surrendering their credentials and authentication codes to gain unauthorized access to corporate platforms for data theft and extortion.
6. Nike Probes Possible Data Breach Claims
Nike is looking into a potential security compromise following claims by the WorldLeaks group that they successfully breached the company’s internal servers. The sportswear corporation has officially launched a formal investigation to determine the validity of the group’s claims and the extent of any data exposure.
For more incidents click here!
📢 Cyber News
7. 1Password Adds Phishing Site Warnings
1Password has introduced a new security feature that proactively alerts users when they land on potential phishing websites. This update aims to prevent credential theft by warning users who might otherwise manually enter their information on deceptive or typosquatted domains.
8. Microsoft Probes Windows 11 Boot Failures
Microsoft is currently looking into reports of Windows 11 systems failing to start following the January 2026 security updates. The problem specifically impacts physical hardware running versions 24H2 and 25H2, resulting in a blue screen error known as UNMOUNTABLE_BOOT_VOLUME.
9. NTSB Probes Waymo Robotaxi Bus Violations
The National Transportation Safety Board has launched an investigation into Waymo robotaxis for failing to stop for school buses in Austin, Texas. While Waymo maintains that its safety performance is superior to human drivers, federal investigators are examining why the vehicles continued to pass buses loading or unloading students even after a software update.
For more news click here!
📈Cyber Stocks
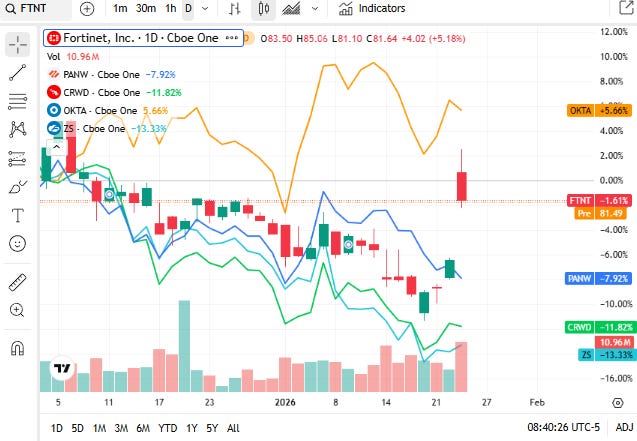
Trading at the start of the week on Monday, 26 January 2026, cybersecurity stocks showed a mixed to constructive tone, supported by renewed interest in tech and resilient demand for security solutions amid ongoing digital threat activity. Rotation within the broader market favored growth sectors, particularly cloud security and identity management names, while select mid-cap cybersecurity names displayed relative stability in a cautious macro environment.
Palo Alto Networks closed near current session levels around 180 dollars and was modestly lower, as platform and cloud security leaders balanced steady enterprise demand against broader tech rotation.
CrowdStrike finished about 452 dollars and was slightly down, reflecting persistent investor focus on long-term cloud and endpoint protection trends even amid short-term profit-taking.
Okta closed around 90.8 dollars and moved modestly lower, with identity and access management stocks tracking broad technology softness.
Zscaler finished near 209.6 dollars and was resilient to weakness, supported by continued interest in zero-trust cloud security adoption.
Fortinet closed about 81.6 dollars and edged higher, as network security hardware and services saw selective buying amid sector rotation.
💡 Cyber Tip
🔥 Fortinet Confirms Active FortiGate SSO Bypass
Fortinet has confirmed that attackers are actively bypassing FortiGate FortiCloud SSO protections, including on fully patched devices. The attack abuses crafted SAML authentication messages to gain administrative access, establish persistence, and exfiltrate firewall configuration data. A comprehensive fix is still in development.
🛠️ What You Should Do
Disable FortiCloud SSO if it is not strictly required
Restrict administrative access from the internet using local policies
Monitor for suspicious administrative logins and unknown user accounts
Review systems for unauthorized configuration exports
Apply Fortinet’s upcoming patches immediately once released
⚠️ Why This Matters
A compromised firewall gives attackers deep control over network traffic, VPN access, and security policies. Until a permanent fix is available, applying temporary mitigations is critical to prevent long term network compromise.
📚 Cyber Book
Outsmarting Business Email Compromise by Philippe Flichy
That concludes today’s briefing. You can check the top headlines here!
Copyright © 2026 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium










“Microsoft is currently looking into reports of Windows 11 systems failing to start following the January 2026 security updates. The problem specifically impacts physical hardware running versions 24H2 and 25H2, resulting in a blue screen error known as UNMOUNTABLE_BOOT_VOLUME.”
nice update here. it’s been interesting to follow a lot of the windows 11 issues.